来源:自学PHP网 时间:2015-04-17 11:59 作者: 阅读:次
[导读] 漏洞一:Parameters.getInstance().data = loaderInfo.parameters;public function get onPlayStart():String{return (_data[onPlayStart]);}ExternalInterface.call(Parameters.getInstance().onPlaySt......
|
漏洞一:
Parameters.getInstance().data = loaderInfo.parameters;
public function get onPlayStart():String{
return (_data["onPlayStart"]);
}
ExternalInterface.call(Parameters.getInstance().onPlayStart, _arg1);
ExternalInterface.call(Parameters.getInstance().onPlayStop);
ExternalInterface.call(Parameters.getInstance().onFileLoadedError);
漏洞二:
function reload(u, show_loading) {
if (show_loading == undefined) {
show_loading = true;
}
if (show_loading) {
_root.loading = new Loading("Loading data...");
}
var _local2 = "";
if (_root.data != undefined) {
_local2 = _root.data;
}
if (u != undefined) {
if (u.length > 0) {
_local2 = u;
}
}
_root.lv = undefined;
_root.lv = new LoadVars();
_root.lv.onLoad = LoadVarsOnLoad;
_root.lv.make_chart = make_chart;
_root.lv.make_pie = make_pie;
_root.lv.load(_local2);
}
漏洞三:
var csPreloader;
loader.loadClip(csPreloader, preloader_mc.target);
漏洞四:
this.loadXML(file);
function init(file, ploader, bookmark, contentpath)
container.init(csConfigFile, preloader_mc, csFilesetBookmark, contentpath);
var csConfigFile;
漏洞五:
getURL(_loc2, this.playList.currentClip().getLinkWindow());
var _loc2 = this.playList.currentClip().getLinkURL();
_loc1.getLinkURL = function ()
{
return (this.linkUrl);
}; www.2cto.com
var _loc1 = (_global.org.flowplayer.playlist.Clip = function (name, baseUrl, fileName, start, end, protected, enableControl, linkUrl, linkWindow, type, allowResize, overlayFileName, overlayId, live, showOnLoadBegin, maxPlayCount, info, thumbnailUrl, suggestedClipsInfoUrl, id, keywords)
{
this.linkUrl = linkUrl;
}
漏洞六:
this.textField.htmlText = ['
', content, '
'].join('');
_global.sIFR = function (textField, content)
{ ……
this.write(content);
……
}
sIFR.instance = new sIFR(_loc3.txtF, _loc4);
_loc4 = sIFR.VERSION_WARNING.split("%s").join(_root.version);
漏洞七:
this._setVar("_onClick", [_root.onclick, pConfig.onclick], "String");
getURL(this._onClick, this._onClickTarget);
顺手写了个简单的检测已知漏洞的flash xss检测脚本:
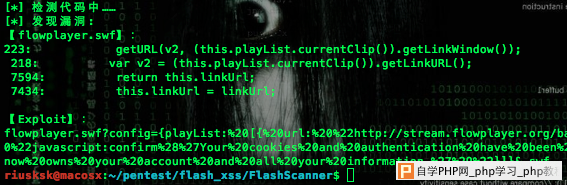 |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com